NSX in an End User Compute Environment
by Curtis Brown
VMware NSX® network virtualisation platform has been around for a little while now delivering an operational model for networking that forms the foundation of the Software-Defined-Data-Centre. It’s often associated more with server virtualisation or as a component within a Cloud Automation solution and with good reason; it’s readily able to deliver a scaled, secure environment, while providing several mechanisms to deliver advanced network functionality such as firewalling, load balancing and anti-malware protection. However, one area where its application is frequently overlooked is in the world of End User Compute – more specifically virtual desktop infrastructure.
Wouldn’t it be nice if…
Consider a full-on Horizon deployment (though, to be fair, these components could be replaced in the most part for an element of your choice) –
- Horizon View – This will publish Virtual Desktops in Pools, with these pools assigned to Active Directory based Groups/Users.
- App Volumes – This gives you a mechanism for delivering defined stacks of applications to the Virtual Desktops.Again, you can assign using Groups or users.
- User Environment Manager – You use this to manage environmental and application settings.
So, you have the mechanisms in place to deliver Virtual Desktops, complete with some granular application and settings delivery. This is all pretty good, but wouldn’t it be nice if you could provide some intelligent network capabilities too?
Finetuned Firewalling.
Now take VMware NSX - this has some nice features that you can leverage in a VDI estate.
One of the key areas of concern is hardening the estate. There’s been a pretty big play in the NSX world around using NSX to provide segmentation – both at a macro level, separating workloads into different VXLANs on virtual switches – and at the micro level using the Distributed Firewall to provide firewall rules at the Vmnic. Both strategies can be used here.
You can also separate Pools at a macro level or a micro level if you wish to, with the latter being particularly interesting.
The Distributed Firewall can provide a great deal of
flexibility when defining firewall rules and can leverage several different
identifiers, including vSphere entities and Active Directory objects. Using these, you can generate a rule bases to
lock down traffic quite tightly, in conjunction with the VDI solution and
application delivery mechanism. Take
this example:
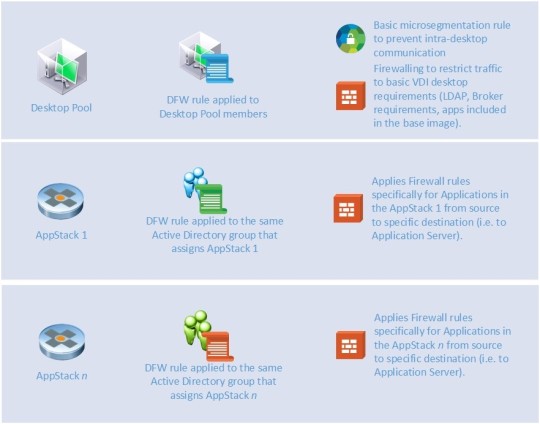
You can set up a standard DFW ruleset that applies to your desktops that will prevent traffic between the virtual desktops, while still providing the core services and application support for anything required for the desktop. This means you can control LDAP traffic between the desktops and Domain Controllers or PCoIP between the desktops, the Connection Servers or direct to physical endpoints if you wish.
With App Volumes, you can define an AppStack with several applications which may well have discrete client/server network traffic requirements. The DFW can apply rules based upon the user logged into the desktop, so you can create and apply rules specific for these client server applications and tie them to the same Active Directory object that applies the AppStack.
The net result is that you end up with a combined ruleset applied to a desktop that is not just tied to a broad pool, but also to discrete needs for users within the pool. This provides strict granular access based upon the needs of the desktop and the application set for the user. And let’s remember that this is applied at the desktop’s connection to the network – not at any perimeter level.
Malware Protection
NSX also provides the ability to integrate a compatible antivirus/antimalware solution into the mix. This is not, however, limited to the more publicised Guest Introspection where virus scanning is offloaded at the hypervisor level. NSX can also integrate with both virtual and physical appliances such as Fortigate for intrusion detection, perimeter firewalling and more.
At the Infrastructure Level
As with any VDI estate, you have the upstream infrastructure to consider, several services can be provided here too.
Using VMware NSX Edge Gateway appliances, you can provide perimeter firewalling between networks.
For Horizon View, both Connection Servers as well as Access Gateways/Security Servers require Load Balancers, as do App Volumes Managers. The NSX Edge appliances are capable of being configured to provide load balancing services.
Perimeter firewalling using NSX Edge can also be provided, so you can have a DMZ layer for the Security Servers/Access Gateways as well.
Generally speaking, you could deploy something like this for
the Horizon View management environment:
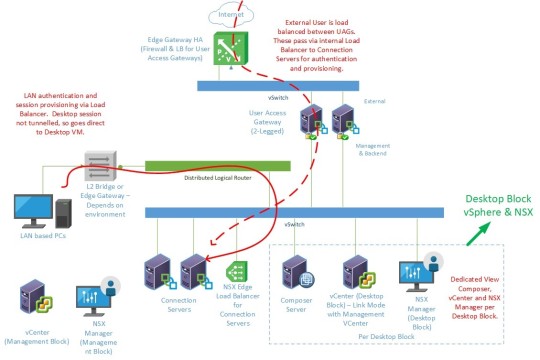
Our external traffic accesses the estate via a pair of NSX Edge Gateways, serving as firewall and load balancer for a pair of VMware User Access Gateways. These are configured as two-legged, tunnelling into the vSwitch beneath, where you have a dedicated NSX Edge appliance load balancing the Connection servers. This internal load balancer is also used by internal users who connect in via an L2 bridge or NSX Edge as appropriate.
You then deploy NSX for the Desktop blocks as well, in order to provide the previously mentioned firewalling and malware protection for a secure end-to-end solution.
Closing Thoughts…
With NSX, it’s possible to turbo-charge the security for a VDI desktop environment in a manner that can be applied regardless of the choice of broker solution – the above would work just as well in a third party VDI solution such as Citrix XenApp or, perhaps more importantly, XenDesktop, not just VMware Horizon. The ability to dynamically set and operate firewalling on egress outside of the guest Operating System means that such firewalling cannot be tampered with from within the VDI desktop, which might be useful in environments where desktops are used with untrusted users (public kiosks for example).
If you’re interested in exploring the combination of VMware NSX network virtualisation in a VDI estate, please contact Xtravirt, and we’d be happy to use our wealth of knowledge and experience to assist you.
About the Author
Curtis Brown joined the Xtravirt consulting team in October 2012. His specialist areas include End User Compute solutions and Virtual Infrastructure design and implementation with particular strength in VDI, storage integration, backup and Disaster Recovery design/implementation. He is a VMware vExpert 2017.