Encryption: Data Protection in VMware Hyper-Converged Infrastructure
By Curtis Brown
Introduction
In the wonderful world of VMware based virtualisation, there has been a concerted effort in recent years to not just virtualise the compute side of matters but expand out into networking (with VMware NSX) and the provisioning of storage (VMware vSAN). This all results in a single VMware Hyper-converged infrastructure offering.
An important factor within this is security. VMware vSphere itself has considerable security with its small footprint, hardened hypervisor and the move towards a hardened Linux based appliance as the preferred option for the VMware vCenter management server. VMware NSX can be argued to be a security product in and off itself – providing not only edge firewalling capabilities but per-VM based firewalling with the Distributed Firewall and support for agentless malware protection solutions with the Guest Introspection framework.
But what of VM storage? SAN solutions can offer security measures, subject to the SAN vendor, but how does this apply in a VMware vSAN environment?
There are two options available:
- VM Encryption
- VMware vSAN Encryption
Each has some pros and cons – so let’s take a look.
VM Encryption
Fundamentally, this is the encryption of virtual machines themselves. There are third party (and, for that matter, in-guest) encryption offerings, but we’ll focus on the built-in VM encryption capability that was released in VMware vSphere 6.5.
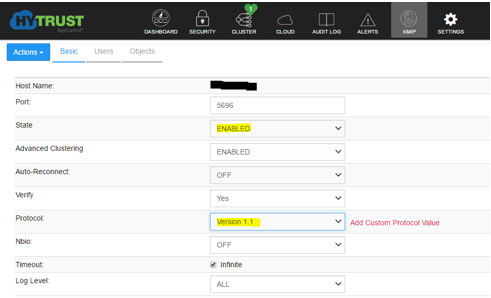
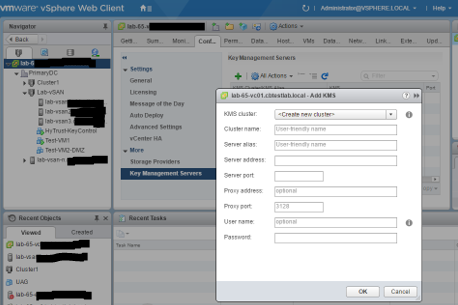
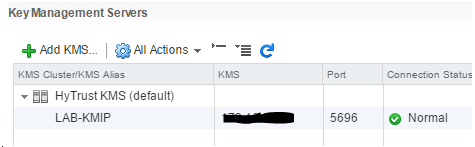
It’s pretty straightforward to set up, requiring only two things – the deployment of an encryption Key Management Server (compatible ones are listed here and in the Interoperability guide) and a VMware vSphere Storage Policy. After that, apply the policy to a given VM and – hey Presto!
So, what’s the catch? The encryption works on all IO operations for the VM itself at the top level – as it’s written to the Virtual Disk. This means that all IO operations in transit are encrypted as well as at rest on the physical disk.
From a security standpoint, this is very secure, and as it’s on a per-VM basis, it’s granular – you don’t need to encrypt everything (though you could argue that this is a management overhead). However, the downside in a vSAN environment is that the encryption occurs before de-duplication, so no space saving is possible.
There are further caveats with VM encryption to be aware of:
- The VM Snapshot ‘Capture the virtual machine
memory’ function is not compatible.
- vSphere Fault Tolerance does not work with VM
encryption.
- Suspending (and resuming) encrypted VMs is not
supported.
In addition, not all vSphere integrated backup solutions can support VM level encryption.
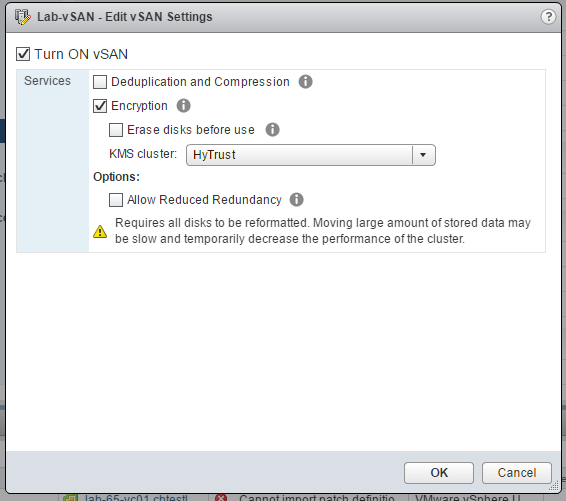
vSAN Encryption
VMware vSAN Encryption uses the same Key Management Server, but this time the VMware vSAN storage is itself encrypted. It’s applied at the cluster level, so anything stored in the vSAN cluster is encrypted – no management overhead as such, but no granularity.
All data travel is in an unencrypted state – it is encrypted when the data hits the caching tier, decrypted when it is de-staged from the cache for de-duplication and writing to the data tier. This means that data-deduplication can be applied in combination with encryption, however the down-side is that encryption is therefore limited to data at rest (i.e. written to disk) as opposed to end-to-end as would be the case for VM encryption.
As encryption is at the storage tier, it is essentially invisible to VM operations – so vSphere operations such as Fault Tolerance and snapshots are fully supported and most vSAN aware backup solutions aren’t impacted.
Comparing the options
To compare these two options:

Closing Thoughts
Both mechanisms have their use cases. VM encryption is the more secure when you consider that it is capable of full end-to-end encryption. It also benefits from being able to support traditional SAN datastores as well as vSAN. However, some VMware vSphere functionality is impaired when compared to vSAN and there is more of a management overhead. In a modern all-flash estate, IO drops caused by encryption are negligible in both cases, so performance should not be a concern.
VM Encryption is worth considering, though it does add a layer of complexity to an estate. If the deployment of a robust KMS (Key Management Server) solution is a must, then there is configuration of the solution itself.
If you’re considering implementing or upgrading a VMware vSphere environment and data security is a concern, please contact Xtravirt, and we’d be happy to use our wealth of knowledge and experience to assist you.
About the Author
Curtis Brown joined the Xtravirt consulting team in October 2012. His specialist areas include End User Compute solutions and Virtual Infrastructure design and implementation with strengths in VDI, storage integration, backup and Disaster Recovery design/implementation. He is a VMware vExpert 2018.